Chapter 5. Unix Clients
In Chapter 3 we showed you how to configure Windows systems to access shared resources on both Windows and Samba servers. This has probably opened up a whole new world of computing for you—one in which you have to run to a Windows system every time you want to copy a file between Unix and Windows! In this chapter, we will show you the "other side"—how to access SMB shares from your favorite Unix system.
You can access SMB resources from Unix in three ways, depending on your version of Unix. A program included with the Samba distribution called smbclient can be used to connect with a share on the network in a manner similar to using ftp when transferring files to or from an FTP site.
If your system is running Linux, you can use the smbfs filesystem to mount SMB shares right onto your Linux filesystem, just as you would mount a disk partition or NFS filesystem. The SMB shares can then be accessed and manipulated by all programs running on the Linux system: command shells, desktop GUI interfaces, and application software.
On some BSD-based systems, including Mac OS X, a pair of utilities named smbutil and mount_smbfs can be used to query SMB servers and mount shares.
For other Unix variants, smbsh can be run to enable common shell commands such as cd, ls, mv, wc, and grep to access and manipulate files and directories on SMB shares. This effectively extends the reach of the Unix shell and utilities beyond the Unix filesystem and into the SMB network.
All the Unix clients can access shares offered by either Windows systems or Samba servers. We have already shown you how to set up a share on a Samba server and could use that as an example to work with. But it's much more fun to use the Unix clients with shares served by Windows systems. So before we start covering the Unix clients in detail, we will take a quick detour and show you how to set up file shares on both Windows 95/98/Me and Windows NT/2000/XP systems.
Sharing Files on Windows 95/98/Me
When sharing files on Windows 95/98/Me, you can authenticate users in two different ways. Share-level security is the default and is easy to use. However, it is not as secure and can require users to type in passwords when connecting to shares. User-level security offers a better security model and can be used if you have either a Samba or Windows NT/2000 server on your network performing user authentication.
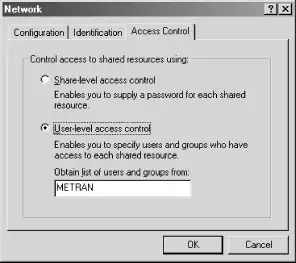
To configure the type of access control for your system, open the Control Panel, double-click the Network icon, then click the Access Control tab. You should see the dialog box shown in Figure 5-1.
Figure 5-1. The Access Control tab of the Windows 98 Network Control Panel window
Click the "Share-level access control" or "User-level access control" radio button, depending on which you want to use. When using user-level access control, you will also need to fill in the name of your workgroup or Windows NT domain. Reboot as requested.
To share a folder, right-click the folder's icon and select Sharing . . . . This will open the Sharing tab of the folder's Properties dialog box. Click the "Shared As:" radio button, and fill in a name for the share (which defaults to the folder's name) and a description, which will be visible to client users. If you don't want the share to be visible in the Network Neighborhood view of other Windows clients, pick a name for the share that ends in a dollar sign ($).
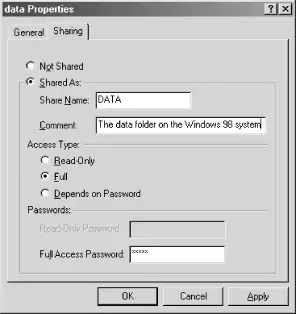
Figure 5-2 shows what the Sharing tab of the folder's Properties dialog box will look like when using share-level security. The security settings are very simple. You can select a radio button for read-only access or full (read/write) access, or have the user's permissions (either read-only or read/write) depend on which password they use. In accordance with which you select, you will be asked to assign either or both of the read-only and full-access passwords for the share.
Figure 5-2. The Sharing tab of the folder's Properties dialog, with share-level security
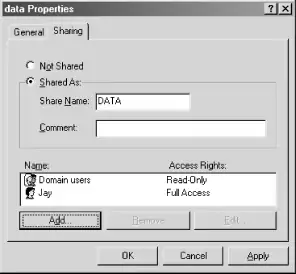
If your system is configured with user-level security, the Sharing tab of the folder's Properties dialog box will look like Figure 5-3. As you can see, we've created a share named "DATA", and used the Add . . . button to create permissions that allow read-only access for all domain users and read/write (full access) for jay.
Figure 5-3. The Sharing tab of the folder Properties dialog, with user-level security
When you are done specifying your settings for the share, click on the OK button, and the share will become available to users on network clients. Unless you chose a share name ending in a dollar sign, you can see it in the Network Neighborhood or My Network Places of Windows clients on the network. You can also now use the Unix clients described in this chapter to connect to the share.
Sharing Files on Windows NT/2000/XP
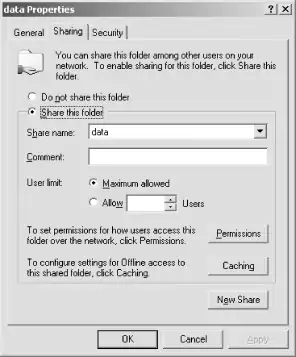
To create a file share on Windows NT/2000/XP, you first must log in to the system as any member of the Administrators, Power Users, or Server Operators groups. Right-click the icon of a folder you wish to share, and click Sharing . . . in the pop-up menu. The Sharing tab of the folder's Properties dialog box will appear, as shown in Figure 5-4. Click the "Share this folder" radio button.
Figure 5-4. The Sharing tab of the folder's Properties dialog on Windows 2000
Share name: will default to the name of the folder, and you can change it if you want. One reason you might want to use a different name for the share is to make the share not appear in browse lists (as displayed by the Network Neighborhood, for example). This can be done by using a share name ending in a dollar sign ($). You can also add a description of the share in the Comment: text area. The description will appear to users of network clients and can help them understand the contents of the share.
By clicking the Permissions button, you can set permissions for the share on a user-by-user basis. This is equivalent to the user-level security of Windows 95/98/Me file sharing. On Windows NT/2000/XP, Microsoft recommends that share permissions be set to allow full access by everyone, with the permissions controlled on a file-by-file basis using filesystem access control lists (ACLs). The actual permissions given to network clients are a combination of the share permissions and file access permissions. To edit the ACL for the folder, click the Security tab. For more information on ACLs, see Section 8.3 in Chapter 8.
If you want, you can limit the number of users who can concurrently connect to the share using the "User limit:" radio button. The New Share button allows you to create multiple file shares for the same folder, each having its own name, comment, user limit, and other parameters.
When you are done, click the OK button, and the folder will be accessible from clients on the network.
smbclient
The Samba Team supplies smbclient as a basic part of the Samba suite. At first, it might seem to be a primitive interface to the SMB network, but smbclient is actually a versatile tool. It can be used for browsing shares on servers, testing configurations, debugging, accessing shared printers, backing up shared data, and automating administrative tasks in shell scripts. And unlike smbfs and smbsh, smbclient works on all Unix variants that support Samba.
In this chapter we'll focus mostly on running smbclient as an interactive shell, using its ftp-like commands to access shared directories on the network. Using smbclient to access printers and perform backups will be covered in Chapter 10.
A complete reference to smbclient is found in Appendix C.
Listing Services
The -L option can be used with smbclient to list the resources on a single computer. Assuming the Samba server is configured to take the role of the master browser, we can obtain a list of the computers in the domain or workgroup like this:
$ smbclient -L toltec
added interface ip=172.16.1.1 bcast=172.16.1.255 nmask=255.255.255.0
Password:
Domain=[METRAN] OS=[Unix] Server=[Samba 2.2.5]
Sharename Type Comment
--------- ---- -------
test Disk For testing only, please
IPC$ IPC IPC Service (Samba 2.2.5)
ADMIN$ Disk IPC Service (Samba 2.2.5)
Server Comment
--------- -------
MAYA Windows 98
MIXTEC Samba 2.2.5
TOLTEC Samba 2.2.5
ZAPOTEC
Workgroup Master
--------- -------
METRAN TOLTECIn the column labeled "Server", maya, mixtec, and zapotec are shown along with toltec, the Samba server. The services on toltec are listed under "Sharename". The IPC$ and ADMIN$ shares are standard Windows services that are used for network communication and administrative purposes, and test is the directory we added as a share in Chapter 2.
Now that we know the names of computers in the domain, we can list services on any of those computers. For example, here is how we would list the services offered by maya, a Windows 98 workstation:
$ smbclient -L maya
added interface ip=172.16.1.1 bcast=172.16.1.255 nmask=255.255.255.0
Password:
Sharename Type Comment
--------- ---- -------
PRINTER$ Disk
HP Printer HP 932C on Maya
D Disk D: on Maya
E Disk E: on Maya
ADMIN$ Disk
IPC$ IPC Remote Inter Process Communication
Server Comment
--------- -------
Workgroup Master
--------- -------A shared printer is attached to maya, so we see the PRINTER$ administrative service, along with the HP share for the printer itself. Also on maya are the D and E shares, which allow access across the network to maya's D: and E: drives. It is normal for the Server and Workgroup sections to be empty when listing services on a Windows client.
Authenticating with smbclient
As with any other SMB client, smbclient needs to supply a username and password if it is authenticating in a domain environment or if it is contacting a Samba server that is set up with user-level security. In a workgroup environment, it will at least need a password to use when connecting with a password-protected resource.
By default, smbclient uses the username of the user who runs it and then prompts for a password. If you are using smbclient a lot, you might tire of entering your password every time.
smbclient supports some alternate methods of entering a username and password. The password can be entered on the command line, like this:
$ smbclient //maya/e jayspassword
Or both the username and password can be supplied by using the -U option, including the username and password separated by a percent (%) character:
$ smbclient //maya/e -U kelly%kellyspassword
This method is useful if you are logged in to the system under an account that is not Samba-enabled or you are testing your configuration to see how it treats another user. With either method, you can avoid having to enter the username and/or password each time you run smbclient by creating an alias for the command or creating a shell function or shell script. For example, with the bash shell, it is possible to define a function like this:
smbcl( )
{
smbclient $* -U jay%jayspassword
}Adding the definition to the shell's startup script (which would be ~/.bash_profile for bash) would result in the definition affecting all subsequent shell invocations.
Another method that can be used to supply both the username and password is to set the USER and PASSWD environment variables. Either set the USER environment variable using the username%password format, or set the USER environment variable to the username, and set PASSWD to the user's password.
It is also possible to create a credentials file containing the username on the first line and the password on the second line, like this:
username = jay password = jayspassword
Then, smbclient is run using the -A option to specify the name of the file:
$ smbclient //maya/e -A ~/.smbpw
NOTE
Of the methods we described in this section, the only one that is really secure is the default method of allowing smbclient to prompt for the password and typing in the password without echoing.
If security is a concern, you definitely should avoid providing your password on the command line because it is very easy for "shoulder surfers" to obtain, as well as anyone who looks through your shell's command history.
If you keep your Samba password in a credentials file, shell startup file, or shell script, make sure the file's permissions prohibit other users from reading or writing it. (Use an octal permissions mode of 0600.) Security experts never keep passwords in files owned by nonroot users or accessible by anyone other than the superuser. As part of their security policy, some organizations do not permit passwords to be stored in files, so you might want to check first before using this method.
The authentication method that uses the USER and PASSWD environment variables isn't any more secure. Environment variables are usually set either on the command line or in one or more of the shell's startup files, so this method suffers from the same weaknesses we've just discussed. In addition, any program run by the user has access to the shell's environment variables, making a Trojan horse attack on the PASSWD variable really easy!
An Interactive smbclient Session
A common use for smbclient is to use it as an ftp-like shell to access SMB resources on the network. To begin a session, smbclient must be provided with the UNC of a resource (which you can find using the -L option) on the command line, like this:
$ smbclient //maya/e added interface ip=172.16.1.3 bcast=172.16.1.255 nmask=255.255.255.0 Password: smb: \>
Forward slashes are accepted by smbclient for the share's UNC, which makes entering the UNC on the command line easier. Backslashes can also be used, but they must be quoted or escaped, and it is somewhat more difficult to type '\\maya\e' or \\\\maya\\e. After connecting to the share, smbclient displays the smb: \> prompt, waiting for a command to be entered. Commands are similar to those with which you might be familiar in ftp and are also somewhat similar to Unix shell commands. To get a list of smbclient commands, use the help command:
smb: \> help ls dir du lcd cd pwd get mget put mput rename more mask del open rm mkdir md rmdir rd prompt recurse translate lowercase print printmode queue cancel quit q exit newer archive tar blocksize tarmode setmode help ? history !
Some commands in the previous list are synonyms for other commands. For example, the ? command is a synonym for help. You can give this command the name of another command as an argument to get a concise reminder of what the command does and how to use it:
smb: \> ? ls
HELP ls:
<mask> list the contents of the current directoryThe term <mask> refers to a file-matching pattern as commonly found in Unix shells and utilities. For example:
smb: \> ls *doc
ms-ProfPol-wp.doc A 131 Tue Dec 18 09:12:34 2002
smbclient.doc A 33969 Mon Dec 10 20:22:24 2002
smbmount.doc A 7759 Mon Dec 10 20:20:00 2002
48590 blocks of size 524288. 40443 blocks availablelists all files ending in "doc" in the current directory on the remote system. In the listing, the leftmost column shows the filename. Moving left to right, we see the file's MS-DOS attributes, then its size, and the time it was last modified.
As with any other Unix utility, smbclient has a working directory on the local host. It also has another current directory on the remote SMB share. With smbclient, the cd command is used to move around on the remote system:
smb: \> cd trans smb: \trans\>
Notice how the prompt changes to reflect the new current working directory. To change your current directory on the local system, use the lcd command:
smb: \trans\> lcd /u/snd the local directory is now /u/snd
Most of smbclient's commands are for performing operations on remote files and directories. There is no command for listing the contents of the local directory. However, smbclient allows a shell escape. Any command preceded by an exclamation point (!) is interpreted as a shell command and is run in a subshell on the local system. For example:
smb: \trans\> ! ls -l total 16 drwxrwxr-x 2 jay jay 4096 Jan 10 14:46 dr220-fet drwxrwxr-x 2 jay jay 4096 Sep 22 12:16 dr220-tube -rw-rw-r-- 1 jay jay 131 Jan 10 02:22 readme.txt drwxrwxr-x 7 jay jay 4096 Jan 10 02:19 xl1
lists the contents of /u/snd. By using smbclient's commands to operate on the remote system—and shell-escaped commands to operate on the local system—it is possible to manipulate data on both systems without having to exit smbclient or open another shell window.
File transfer is performed using the get and put commands. The get command transfers a single file from the remote to the local system, and the put command copies a file from the local to the remote system. For example, the following command copies the file readme.txt to the SMB share:
smb: \trans\> put readme.txt putting file readme.txt as \trans\readme.txt (127.9 kb/s) (average 10.7 kb/s)
NOTE
Unlike ftp, smbclient does not have ascii and binary commands to set the type of the file that is being transferred. Before transferring a text file from a Unix system to a Windows or Macintosh system, you might want to use the GNU unix2dos command to reformat newlines in the file to work with the carriage return linefeed (CRLF) standard:
$ unix2dos text_file >text_file.txtand then transfer the CRLF-formatted version. After transferring a text file from a Windows or Macintosh system to Unix, you can use the GNU dos2unix command to perform the inverse operation:
$ dos2unix text_file.txt >text_file
To transfer more than one file with a single command, you can use the mget and mput commands, which accept a list of filenames in the command line. The list can be provided by typing in the filenames on the command line separated by spaces, or the group of files can be specified with a pattern as one would use in Unix shell commands. The command:
smb: \trans\> mget plain/*
copies all the files in the directory plain on the SMB share to the current directory on the local system. By default, smbclient prompts for each file, asking if you want to copy it:
smb: \trans\> mget plain/* Get file tomm.wav? n Get file toml.wav? n Get file tomh.wav? n Get file snare.wav? n Get file rim.wav? n Get file handclap.wav? n Get file bassdrum.wav? n
If you are sure you want to copy all the files, you can turn off prompting with the prompt command, like this:
smb: \trans\> prompt prompting is now off
By default, if you specify the name of a directory, smbclient will not copy the contents of the directory. To transfer the entire contents of directories listed in the mput or mget command, you must first use the recurse command:
smb: \trans\> recurse directory recursion is now on
After setting things up with the prompt and recurse commands, we can copy a directory like this:
smb: \trans\> mget acc getting file tomm.wav of size 55494 as tomm.wav (2580.6 kb/s) (average 2087.3 kb/s) getting file toml.wav of size 57220 as toml.wav (2660.9 kb/s) (average 2167.6 kb/s) getting file tomh.wav of size 55936 as tomh.wav (2601.2 kb/s) (average 2220.8 kb/s) getting file snare.wav of size 22132 as snare.wav (1200.7 kb/s) (average 2123.7 kb/s) getting file rim.wav of size 8314 as rim.wav (1623.8 kb/s) (average 2110.8 kb/s) getting file handclap.wav of size 14180 as handclap.wav (1978.2 kb/s) (average 2106.2 kb/s) getting file bassdrum.wav of size 6950 as bassdrum.wav (2262.3 kb/s) (average 2108.5 kb/s)
Directory recursion applies to all commands, so if an ls command is used while directory recursion is on, all files in the directory tree are listed. To turn directory recursion off again, simply re-enter the command. At the same time, you might also wish to toggle prompting back to its initial state:
smb: \trans\> recurse directory recursion is now off smb: \trans\> prompt prompting is now on
There are other smbclient commands that you might find useful. The mkdir command can be used to create a directory; rmdir removes a directory; rm deletes a file; and rename changes a file's name. These behave very similarly to their Unix shell counterparts. Appendix C contains a complete reference to smbclient and its command set.
To exit smbclient, use the exit or quit command:
smb: \trans\> quit
Programming with smbclient
The -c option of smbclient allows a list of commands to be passed on the command line. To copy the file \\maya\e\trans\readme.txt to /u/snd/readme.txt, we might use the command:
$ smbclient //maya/e -c "lcd /u/snd; cd trans; get readme.txt" -A ~/.smbpw
Everything that smbclient needs to know to perform the operation has been specified in the command. There is no interactive session, so a command such as this can be placed inside a shell script or a program in some other programming language.
By using smbclient in this manner, it is possible to create customized commands using shell functions, scripts or aliases. For example, suppose we wanted a command to print a short listing of files in a shared directory, showing just the names of the files. Using a bash function, we could define a command smbls as follows:
smbls( )
{
share=`echo $1 | cut -d '/' -f '1-4'`
dir=`echo $1 | cut -d '/' -f '5-'`
smbclient $share -c "cd $dir; ls" -A ~/.smbpw | \
grep "^ " | cut -d ' ' -f 3 - | sort
}After defining this function, we can use smbls like this:
$ smbls //maya/e CD-images lectures ms-ProfPol-wp.doc profile-map readme.txt RECYCLED smbclient.doc smbmount.doc smbsh.txt trans $ smbls //maya/e/lectures . .. lecture1.mp3 lecture2.mp3 lecture3.mp3 lecture4.mp3 lecture5.mp3 lecture6.mp3 lecture7.mp3 lecture8.mp3 lecture9.mp3
Another use for smbclient in scripts is performing administrative tasks. Suppose a group of users on Windows clients are sharing a set of files as part of a project on which they are working. Instead of expecting them to coordinate making daily backups, we could write a script that copies the share to the Samba server and run the script nightly as a cron job. The directory on the Samba server could be shared as well, allowing any of the users to retrieve a backup file on their own, without having to bother an administrator.
Backups with smbclient
A major use of smbclient is to create and restore backups of SMB file shares. The backup files smbclient writes are in tar format, making them easy to work with and portable among all Unix versions. Using smbclient on a Unix server to run network backups can result in a more centralized and easily managed solution for providing data integrity because both SMB shares and NFS filesystems can be backed up on the same system.
You can use smbclient to perform backups in two ways. When backing up an entire share, the simplest method is to use the -Tc option on the command line:
# smbclient //maya/e -A samba-domain-pw -Tc >maya-e.tar
This will create a tar archive of the \\maya\e share in the file maya-e.tar. By using the -D option, it is possible to back up a directory in the share, rather than the whole share:
# smbclient //maya/e -A samba-domain-pw -D trans -Tc >maya-e.tar
This causes smbclient to change its working directory to the trans directory of the \\maya\e share before starting the backup. It is also possible to use smbclient's tar command in interactive mode, like this:
# smbclient //maya/e added interface ip=172.16.1.3 bcast=172.16.1.255 nmask=255.255.255.0 Password: smb: \> cd trans smb: \trans\> tarmode full hidden system quiet smb: \trans\> tar c maya-e-trans.tar
With the previous code, only the trans subdirectory in the \\maya\e share will be backed up, using the settings specified in the tarmode command. To have this type of backup run automatically from a script, use the -c option:
# smbclient //maya/e -A samba-domain-pw -c "cd trans; tarmode full hidden \
system quiet; tar >maya-e-trans.tar"Using either the -T command-line option or smbclient's tar command, additional options can be supplied. It is necessary to specify either the c option to create a backup archive or the x option to extract (restore) one.[1]
The other options can be appended to the option string and are explained in the section on smbclient in Appendix C. They allow you to create incremental backups, specify which files to include or exclude from the backup, and specify a few other miscellaneous settings. For example, suppose we wish to create an incremental backup of a share and reset the archive bit on the files to set things up for the next incremental backup. Instead of using the interactive commands:
smb: \> tarmode inc reset quiet smb: \> tar c backup.tar
we could either use the interactive command:
smb: \> tar cgaq backup.tar
or specify the -Tcgaq option on the smbclient command line.
Your best strategy for using smbclient for network backups depends on your local configuration. If you have only a few Windows systems sharing a small amount of data, you might create a script containing smbclient -Tc commands to back up each share to a separate tar file, placing the files in a directory that is included with regular backups of the Unix system. If you have huge SMB shares on your network, you might prefer to write the backup directly to a tape drive. You can do this with smbclient just as you would with a Unix tar command:
# smbclient //maya/d -A samba-domain-pw -Tc >/dev/tape
After you have become more familiar with smbclient and have an automated backup system in place, you might find that using Samba has dramatically decreased your anxiety regarding the integrity of your network's data. The authors of this book are experienced Unix system administrators, and we highly recommend having a backup strategy that has been carefully planned, implemented, and most importantly, tested and known to work as it is supposed to.
smbfs
On Linux, the smbfs filesystem can be used to mount SMB shares onto the Linux filesystem in a manner similar to mounting disk partitions on NFS filesystems. The result is so transparent that users on the Linux system might never be aware that they are accessing files through a Windows or Samba server. Files and directories appear as any other files or directories on the local Linux system, although there are a few differences in behavior relating to ownership and permissions.[2]
Although smbfs is based on the Samba code, it is not itself part of the Samba distribution. Instead, it is included with Linux as a standard part of the Linux filesystem support.
The smbmount and smbmnt programs are part of the Samba distribution and are needed on the client to mount smbfs filesystems. Samba must be compiled with the --with-smbmount configure option to make sure these programs are compiled. They refer to smb.conf for information they need regarding the local system and network configuration, so you will need a working smb.conf file on the system, even if it is not acting as a Samba server.
Mounting an smbfs Filesystem
The smbmount command is used to mount an smbfs filesystem into the Linux filesystem. The basic usage is:
# smbmount Share-UNC mount-point -o options
Replace Share-UNC with the UNC for the SMB share, and mount-point with the full path to the directory in the Linux filesystem to use as the mount point. The options argument is used to set the exact manner in which the share is mounted. Let's look at an example of a smbmount command:
# smbmount //maya/e /smb/e \
-o "credentials=/home/jay/.smbpw,uid=jay,gid=jay,fmask=664,dmask=775"Here we are mounting share \\maya\e from a Windows 98 system on the mount point /smb/e on the Linux system.
NOTE
If your Linux kernel doesn't include smbfs support, you will get the error message:
ERROR: smbfs filesystem not supported by the kernelIn this case, you must configure and compile a new kernel to include support for smbfs. When smbfs is installed, and an SMB share is mounted, you can run the command:
$ cat /proc/filesystemsand see a line that looks like:
nodev smbfsin the command's output.
The mount point must exist before smbmount is run and can be created using the mkdir command:
# mkdir /smb/e
The argument to the -o option might look a little complex. It is a comma-separated list of key=value pairs. The credentials key is set to the name of the credentials file, which is used to give smbmount a valid username and password with which to authenticate while connecting to the share. The format is identical to that used by smbclient (as explained in the previous section), so you can use the same credentials file for both clients. If you want, you can use the key=value pair username=name%password to specify the username and password directly in the smbmount command, although this is considerably less secure.
TIP
The smbmount command accepts the same authentication methods as smbclient. The comments in the section on smbclient regarding supplying passwords on the command line—and keeping passwords in files and environment variables—also apply here.
The rest of the options tell smbmount how to translate between the SMB filesystem and the Unix filesystem, which differ in their handling of ownership and permissions. The uid and gid options specify the owner and group to be assigned to all directories and files in the mounted share.
The fmask and dmask options specify bitmasks for permissions of files and directories, respectively. These bitmasks are logically ANDed with whatever permissions are granted by the server to create the effective permissions on the client Unix system. On the server side, the permissions granted depend on the server's operating system. For a Windows 95/98/Me server using share-mode security, the MS-DOS read-only attribute can be set on individual files and directories and combined with the Full Access or Read Only permissions on the share as a whole. In user-level security mode, Windows 95/98/Me can have ACL-like permissions applied to the entire share, as discussed in Chapter 4. Windows NT/2000/XP support ACLs on individual files and directories, with Full Control, Change, or Read permissions that can be applied to the entire share. If the server is a Samba server, the permissions are whatever is defined by the Samba share and the local Unix system for the individual files and directories. In every case, the permissions applied to the share act to further limit access, beyond what is specified for the individual files and directories.
TIP
You might think that the fmask and dmask permission masks can be used only to reduce the effective permissions on files and directories, but this is not always the case. For example, suppose that a file is being shared by a Windows 95/98/Me server using share-mode security and that some number of users have been given the Full Access password for the share. If the share is mounted with smbmount using an fmask of 666, read/write permissions are granted on the Unix system not only for the owner, but for everyone else on the Unix system as well!
After mounting the \\maya\d share to /smb/e, here is what the contents of /smb/e look like:
$ cd /smb/e ; ls -l total 47 drwxrwxr-x 1 jay jay 512 Jan 8 20:21 CD-images drwxrwxr-x 1 jay jay 512 Jan 6 21:50 lectures -rw-rw-r-- 1 jay jay 131 Dec 18 09:12 ms-ProfPol-wp.doc -rw-rw-r-- 1 jay jay 59 Dec 18 09:12 profile-map -rw-rw-r-- 1 jay jay 131 Jan 15 05:01 readme.txt drwxrwxr-x 1 jay jay 512 Feb 4 2002 RECYCLED -rw-rw-r-- 1 jay jay 33969 Dec 10 20:22 smbclient.doc -rw-rw-r-- 1 jay jay 7759 Dec 10 20:20 smbmount.doc -rw-rw-r-- 1 jay jay 1914 Dec 10 20:17 smbsh.txt drwxrwxr-x 1 jay jay 512 Jan 10 03:54 trans
For the most part, the files and directories contained in the mounted smbfs filesystem will work just like any others, except for limitations imposed by the nature of SMB networking. For example, not even the superuser can perform the operation:
# chown root lectures chown: changing ownership of 'lectures': Operation not permitted
because SMB shares do not intrinsically support the idea of ownership. Some odd behaviors can result from this. For example, the command:
# chmod 777 readme.txt
does not produce an error message, although nothing has been changed. The file readme.txt still has permissions set to 664:
# ls -l readme.txt -rw-rw-r-- 1 jay jay 131 Jan 15 05:01 readme.txt
Aside from little things such as these, the mounted smbfs filesystem can be used in conjunction with virtually any application, and you might be pleasantly surprised at how nicely it integrates with your Linux-based computing environment. You can even create symbolic links in the Unix filesystem, pointing to files and directories inside SMB shares. However, unless the server is a Samba server that supports Unix CIFS extensions, you will not be able to create a symbolic link inside the mounted smbfs filesystem.
Mounting smbfs Filesystems Automatically
As with other types of filesystems, an smbfs filesystem can be mounted automatically during system bootup by creating an entry for it in /etc/fstab. The format for the entry is as follows:
Share-UNC mount-point smbfs options 0 0
Replace Share-UNC with the UNC of the share (using the forward slash format), and replace mount-point with the name of the directory in the Linux filesystem on which the share will be mounted. In place of options, simply use the string that you used with the -o flag in the smbmount command.
Once you have found the arguments to use with the smbmount command to mount the share the way you like it, it is a very simple matter to create the entry for /etc/fstab. The smbmount command we used to mount the share \\maya\e on /smb/e would translate to this /etc/fstab entry:
//maya/e /smb/e smbfs credentials=/home/jay/.smbpw,uid=jay,gid=jay,fmask=664,dmask=775 0 0 (Please note that this should all go on one line.)
WARNING
If you make a mistake in modifying /etc/fstab, your system might not reboot properly, and you might be forced to boot into single-user mode to fix the problem. Before you edit /etc/fstab, be sure to make a backup copy of it, and be prepared to recover your system if anything goes wrong.
Once the entry has been added, the system will automatically mount the share when booting. Or, the system administrator can manually mount or unmount the share with commands such as these:
# mount /smb/e # umount /smb/e
TIP
It is possible to use mount and umount by giving them the UNC for the share using forward slashes, as in our /etc/fstab entry. However, be careful about this. A share might be listed more than once in /etc/fstab so that it can be mounted at more than one place in the Linux filesystem. If you use the UNC to specify the share you wish to mount or unmount, you might cause it to be mounted or unmounted at another mount point from the one you intended.
Common smbmount Options
Table 5-1 lists key=value pairs that can be used with the -o option of smbmount or in the options field of the /etc/fstab entry for the smbfs filesystem. See the smbmount manual page for a complete list of options.
Table 5-1. smbmount options
smbsh
The smbsh program is part of the Samba suite and works on some, but not all, Unix variants.[3] Effectively, it adds a wrapper around the user's command shell, enabling it and common Unix utilities to work on files and directories in SMB shares, in addition to files and directories in the local Unix filesystem. From the user's perspective, the effect is that of a simulated mount of the SMB shares onto the Unix filesystem.
smbsh works by running the shell and programs run from it in an environment in which calls to the standard C library are redirected to the smbwrapper library, which has support for operating on SMB shares. This redirection can work only if the program being run is dynamically linked. Fortunately, modern Unix versions ship with most common utilities linked dynamically rather than statically.
TIP
To determine whether a program is dynamically or statically linked, try using the file command.
To use smbsh, your Samba installation must be configured using the configure option --with-smbwrapper.
If you have a number of Unix systems with the same host operating system and architecture and don't want to bother with a full Samba installation, you can simply move the following files to the other systems:
/usr/local/samba/bin/smbsh /usr/local/samba/bin/smbwrapper.so /usr/local/samba/lib/smb.conf
Make sure that /usr/local/samba/bin is in your shell's search path. The smb.conf file is needed only for smbsh to determine the workgroup or domain and does not need to be as elaborate as your Samba server's configuration file.
An Interactive Session with smbsh
To start smbsh, simply type in the smbsh command at the shell prompt. You will be prompted for a username and password with which to authenticate on the SMB network:
$ smbsh Username: davecb Password: smbsh$
While working within the smbsh shell, you have a virtual /smb directory. This does not actually exist in the Unix filesystem and is supported within smbsh only to help organize the SMB shares in a structure familiar to Unix users. You can list the contents of the /smb virtual directory and get a list of workgroups in the local network, which are also presented as virtual directories:
smbsh$ cd /smb ; ls ZOOL PLANK BACIL
You can change your working directory to one of the workgroup virtual directories, and listing one of them will show the computers in the workgroup:
smbsh$ cd ZOOL ; ls ANTILLES DODO MILO SEAL ARGON HANGGLIDE OSTRICH SPARTA BALLET INFUSION PLAQUE THEBES CHABLIS JAZ PRAETORIAN TJ COBRA KIKO RAYOPCI TRANCE COUGUR MACHINE-HEADPCI RUMYA VIPERPCI CRUSTY MATHUMA SCOT
Likewise, you can change your current directory to, and list the contents of, a computer virtual directory, and then you can see a listing of shares offered by that computer:
smbsh$ cd scot ; ls ADMIN$ davecb nc np2s pl ace dhcp-mrk03 np nps xp cl ep np2 opcom
This is the lowest level of smbsh's virtual directory system. Once you cd into a share, you are within the SMB share on the remote computer:
smbsh$ cd davecb ; ls Mail mkanalysis_dirs.idx SUNWexplo nfs.ps Sent nsmail allsun.html projects.txt bin sumtimex
Once in a remote share, most of the Unix shell utilities will work, and you can operate on files and directories much as you would on any Unix system. You can even create symbolic links in the Unix filesystem pointing to files and directories in the SMB share. However, attempts to create symbolic links in the SMB share will fail unless the share is being served by Samba with support for Unix CIFS extensions.
smbutil and mount_smbfs
The smbutil and mount_smbfs programs provide SMB client functionality for FreeBSD, Darwin, and Mac OS X. Neither of the programs is part of the Samba distribution; however, we are including them to give you a little additional support in case you have BSD-related Unix systems on your network.
smbutil
The smbutil program provides functionality similar to some of the Samba suite's command-line utilities. It can be used to list the shares available on an SMB server or perform NetBIOS name lookups.
The first argument given to smbutil is one of a number of subcommands and is usually followed by arguments specific to the subcommand. For example, to list the resources offered by a server, use the view subcommand, and enter your server password when prompted:
% smbutil view //vamana Password: Share Type Comment ------------------------------------------------------------- public disk SS2500 printer Stylus Scan 2500 IPC$ pipe IPC Service (Samba 2.2.5) ADMIN$ disk IPC Service (Samba 2.2.5) leonvs disk User Home Directories 5 shares listed from 5 available
If you wish to connect to the server with a username that differs from that on your client, you can specify it on the command line by preceding the name of the server with the username and using an at sign (@) as a separator:
% smbutil view //leonvs@vamana
You can also include the password after the username, using a colon (:) as a separator, to avoid being prompted for it:
% smbutil view //leonvs:leonspassword@vamana
Typing your password in the open like this is strongly discouraged. It's a little better if you use an encrypted password, which you can generate using smbutil's crypt subcommand:
% smbutil crypt leonspassword $$1625a5723293f0710e5faffcfc6
This can then be used in place of a clear-text password. However, the encryption is not particularly strong and will foil only the most casual inspection. As noted earlier, the only reasonably secure method of providing a password is to be prompted for it.
While starting up, smbutil reads the file .nsmbrc in the user's home directory. Also, the file /usr/local/etc/nsmb.conf is read, and directives in that file override those in users' ~/.nsmbrc files. This is to allow administrators to apply mandatory settings to all users. Directives can be placed in this file using the section and parameter format similar to that of the Samba configuration file. A list of common configuration parameters is given in Table 5-2.
For example, to keep your password in your ~/.nsmbrc file, you can create an entry in the file such as the following:
[VAMANA:LEONVS]
password=$$1625a5723293f0710e5faffcfc6The section heading in brackets specifies the SMB server's NetBIOS name and the username to which the subsequent parameter settings apply. (The hostname and username should be supplied in uppercase characters.) Section headings can also consist of just a hostname or can contain a share name as a third element for specifying parameters applicable to a single share. Finally, if a [default] section is present, the settings in it apply to all connections.
The following example .nsmbrc shows some of the other parameters you might use:
[default]
username=leonvs
# NetBIOS name server
nbns=192.168.1.3
[VAMANA]
# server IP address
addr=192.168.1.6
workgroup=TEST
[VAMANA:LEONVS]
password=$$1625a5723293f0710e5faffcfc6Another thing you can do with smbutil is translate between IP addresses or DNS names and NetBIOS names. For example, the status subcommand takes an IP address or DNS hostname as an argument and returns the corresponding SMB server's NetBIOS name and workgroup:
% smbutil status 192.168.1.6 Workgroup: TEST Server: VAMANA
The lookup subcommand returns the IP address associated with a given NetBIOS hostname. A NetBIOS name server can be optionally specified with the -w argument:
% smbutil lookup -w 192.168.1.3 VAMANA Got response from 192.168.1.3 IP address of VAMANA: 192.168.1.6
mount_smbfs
The mount_smbfs program performs essentially the same function as smbmount on Linux. It mounts an SMB share on a directory in the local filesystem. The SMB share can then be accessed just like any other directory, subject to some behavioral differences noted earlier in Section 5.4.1.
The command synopsis for mount_smbfs is:
mount_smbfs [options] Share-UNC mount-point
where Share-UNC is of the form:
//[workgroup;][username[:password]@]server[/share]
For example:
# mount_smbfs '//TEST;leonvs:$$1625a5723293f0710e5faffcfc6@vamana/leonvs' / \Volumes/leonvs
The ownership and permissions of the mount point determine the default ownership and permissions for files and directories in the mounted share. These can be modified with command-line arguments, like this:
# mount_smbfs -u leonvs -g admin -f 0750 -d 0755 //leonvs@vamana/leonvs \/Volumes/leonvs
In this example, the files and directories in the mounted share will be owned by the user leonvs and the group admin, with files and directories having permissions 750 and 755, respectively. (As usual, the permissions are specified in the octal format used by the Unix chmod command.)
The mount_smbfs command also makes use of settings in /usr/local/etc/nsmb.conf and ~/.nsmbrc, as described earlier. A list of common configuration parameters and command-line options is provided in Table 5-2.
Table 5-2. Common smbutil and mount_smbfs options
|
Command-line option |
Configuration file parameter |
Description |
|---|---|---|
|
-I hostname |
addr |
Avoid NetBIOS name resolution and connect to the server using the specified DNS hostname or IP address. |
|
-N |
none |
Do not prompt for a password. |
|
-R count |
retry_count |
Number of times to retry connection before giving up. |
|
-T seconds |
timeout |
Timeout, in seconds, per connection request. |
|
-U username |
username |
Username to use for authentication. Defaults to Unix username. |
|
-W workgroup |
workgroup |
Name of workgroup of remote server. |
|
-d mode |
none |
Permissions to apply to directories in the mounted share. Defaults to the same as the file permissions, plus an execute (search) bit whenever the read bit is set. |
|
-f mode |
none |
Permissions to apply to files in the mounted share. Defaults to the same as the permissions set on the directory used as the mount point. |
|
-g group |
none |
Name or numeric GID to apply to all files and directories in the mounted share. Defaults to the group of the directory used as the mount point. |
|
-n long |
none |
Disable support for long filenames. Restrict filenames to 8.3 naming standard. |
|
-u username |
none |
Username or numeric UID to apply as the owner of all files and directories in the mounted share. Defaults to the owner of the directory used as the mount point. |
|
-w hostname |
nbns |
Hostname or IP address of the NetBIOS name server. |
|
none |
password |
Password to use for authentication. |
Mac OS X
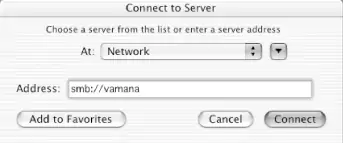
In addition to smbutil and mount_smbfs, OS X includes a graphical interface to the functionality they provide. To use this interface, open the Go menu and select the Connect to Server . . . menu item. Instead of using a UNC, specify the share in the form of a Uniform Resource Identifier (URI) with a prefix of smb:// entered in the Address field, as shown in Figure 5-5.
Figure 5-5. OS X Connect to Server dialog
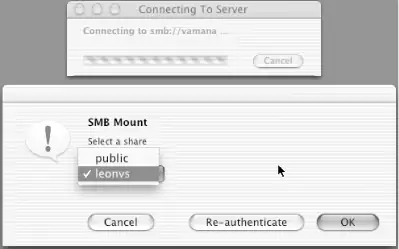
You can specify a server, share, workgroup, username, and password (optionally encrypted with smbutil crypt) in the URI, in the same format as the UNC argument to mount_smbfs. If you don't specify a share name in the URI, you will be shown a window that lets you choose from a list of shares available to mount. See Figure 5-6.
Figure 5-6. Selecting a share to mount
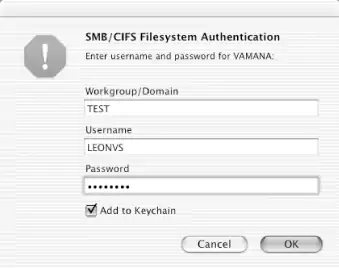
Only guest-accessible shares will show up in the list until you've authenticated. After pressing the Authenticate button, you'll be prompted for a workgroup, username, and password, as shown in Figure 5-7. You'll also see this dialog if you provide a share name in the URI, but not a username and password.[4]
Figure 5-7. Client authentication
As usual for Mac OS X, shares are mounted under /Volumes, but show up in the root of the Finder hierarchy.
If you have a WINS server on your network, you can provide the server's IP address in the Directory Access application, or by using the wins server parameter in /etc/smb.conf.
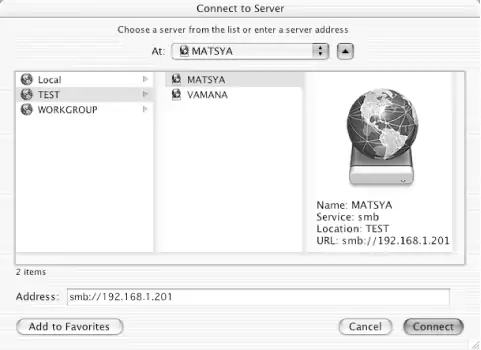
If you don't know the name of a server to which you wish to connect, you can look for it in the browse list, using the graphical frontend to the nmblookup command provided with Samba. Click the downward-pointing arrow in the Connect to Server . . . dialog box to show a hierarchical, column-based view of available workgroups and servers, similar to that shown in Figure 5-8. If your client is also acting as an SMB file server, it won't show up in its own browse list.
Figure 5-8. Browsing the network
Footnotes
[1] An alternative to extracting the tar archive directly to the SMB share is to use the Unix system's tar command to extract it to a directory on the Unix server, then copy the desired file(s) to a shared directory. This allows a greater amount of control over the restoration process, as when correcting for an accidental file deletion or reverting a set of files to a previous condition.
[2] Samba Versions 2.2.4 and later have support for Unix CIFS extensions developed by Hewlett-Packard, which add full support for Unix ownership, group, and permissions in smbfs filesystems when shared between two Samba systems. You will also need a recent version of smbfs in your Linux kernel.
[3] At the time of this writing, smbsh does not work on HP/UX or Linux. However, Linux support might return in the future.
[4] If you've previously stored your authentication information in a Keychain, you will instead be prompted for your Keychain password.